
All times listed in Local Time in China
Day 1 Monday, Oct. 20 | Day 2 Tuesday, Oct. 21 | Day 3 Wednesday, Oct. 22 | Day 4 Thursday, Oct. 23 |
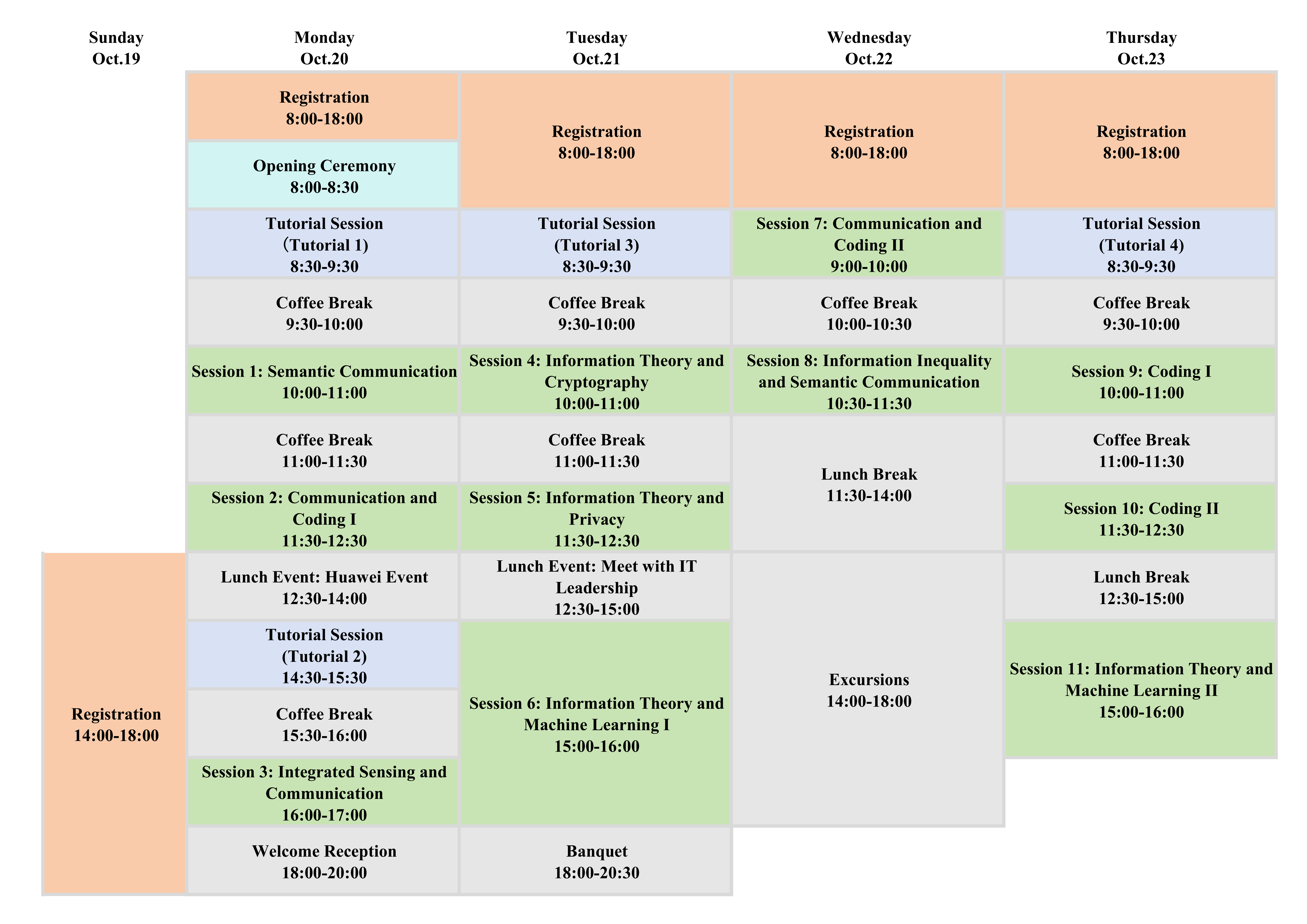
· Day 1 - Monday, Oct. 20 | ||
8:00-18:00 | Registration Desk | 1F, Lobby |
8:30-9:30 | Tutorial 1: Semantic Information Theory: Rate-distortion Approaches Wenyi Zhang, Professor, University of Science and Technology of China | B1, Meeting Room Ⅱ |
9:30-10:00 | Coffee Break | B1, Banquet Hall Corridor |
10:00-11:00 | Session 1: Semantic Communication Invited Talk 1: If Rand()%10 is Bad, How to Use TRNG Efficiently? Hsin-Po Wang, Assistant Professor, National Taiwan University Invited Talk 2: Token-Level Communication and Editing in the Era of Large Language Models Xueyan Niu, Principal Engineer, Huawei Technologies Co., Ltd. Learning-based Joint Geometric-ProbabiIistic Shaping for DigitaI Semantic Communication Wei Liu, University of Science and Technology of China; Shuo Shao,University of Shanghai for Science and Technology; Wenyi Zhang,University of Science and Technology of China | B1, Meeting Room Ⅱ |
11:00-11:30 | Coffee Break | B1, Banquet Hall Corridor |
11:30-12:30 | Session 2: Communication and Coding I Invited Talk 3: On the Fundamental Limits of Generative Communication Jun Chen,Professor,McMaster University Quickest Change Detection of Network Structure in Forest Ising ModeIs Frank Lin, Academia Sinica; I-Hsiang Wang, National Taiwan University Invited Talk 4: On Short Linear Codes with Nearly Optimal Asymptotic Frame Error Rate Wai Ho MOW, Professor,The Hong Kong University of Science and Technology | B1, Meeting Room Ⅱ |
12:30-14:00 | Lunch Event: Huawei Event Title: Challenges from Theory Lab Ting-Yi Wu (Ivan), Expert, Huawei Technologies Co., Ltd. | B1, Meeting Room Ⅱ |
14:30-15:30 | Tutorial 2: Coding for Distributed Storage: Past, Present, and Future Jie Li, Senior Researcher, Huawei Technologies Co., Ltd., Hong Kong | B1, Meeting Room Ⅱ |
15:30-16:00 | Coffee Break | B1, Banquet Hall Corridor |
16:00-17:00 | Session 3: Integrated Sensing and Communication Unbounded MuIti-Letter MarginaI Gain for Bistatic Integrated Sensing and Communication Xinjie Yuan, Tsinghua Shenzhen International Graduate School, Tsinghua University; Tianren Peng, Tsinghua Shenzhen International Graduate School, Tsinghua University; Haohao Fu, Tsinghua Shenzhen International Graduate School, Tsinghua University; Shao-Lun Huang, Tsinghua Shenzhen International Graduate School, Tsinghua University MuIti-Ietter AnaIysis of MarginaI Rate-Fisher Information Tradeoff: Unbounded Gain Xinjie Yuan, Tsinghua Shenzhen International Graduate School, Tsinghua University; Tianren Peng, Tsinghua Shenzhen International Graduate School, Tsinghua University;Haohao Fu, Tsinghua Shenzhen International Graduate School, Tsinghua University; Shao-Lun Huang, Tsinghua Shenzhen International Graduate School, Tsinghua University Unbounded Computing Gain for Joint Coding over Reversed Combination Networks Xiufang Sun, Nankai University; Shanshan Li, Nankai University; Delong Li, Nankai University; Xuan Guang; Nankai University | B1, Meeting Room Ⅱ |
18:00-20:00 | Welcome Reception | B1, Meeting Room Ⅰ |
· Day 2 - Tuesday, Oct. 21 | ||
8:00-18:00 | Registration Desk | 1F, Lobby |
8:30-9:30 | Tutorial 3: Information-theoretic Cryptography Shun Watanabe,Associate Professor,Tokyo University of Agriculture and Technology | B1, Meeting Room Ⅱ |
9:30-10:00 | Coffee Break | B1, Banquet Hall Corridor |
10:00-11:00 | Session 4: Information Theory and Cryptography Invited Talk 5: Source Models for the Byzantine Generals Problem and Byzantine Distributed Function Computation Vinod M. Prabhakaran, Associate Professor,Tata Institute of Fundamental Research, India Invited Talk 6: Information-Theoretic Security, Revisited Mitsugu Iwamoto,Professor,University of Electro-Communications Chaos-Based Cryptography Using DuaI-channeI Switching Chien-Shu Hsieh, Chinese Culture University; Chang-Ming Wu, Chung Yuan Christian University | B1, Meeting Room Ⅱ |
11:00-11:30 | Coffee Break | B1, Banquet Hall Corridor |
11:30-12:30 | Session 5: Information Theory and Privacy Invited Talk 7: On the Source Model Key Agreement Problem Amin Gohari, Vice-Chancellor Associate Professor, The Chinese University of Hong Kong Invited Talk 8: Differential Privacy over Affine Manifolds Guodong Shi, Associate Professor, The University of Sydney Bounds for IndividuaI Keys in Vector Linear Secure Aggregation Zhou Li, Guangxi University; Wenting Shi,Guangxi Beitou Xinchuang Technology Investment Group Company Limited;Haiqiang Chen, Guangxi University; Jihao Fan, Southeast University | B1, Meeting Room Ⅱ |
12:30-15:00 | Lunch Event: Meet with IT Leadership ● Yunjiang Wang,Professor, Secretary-General of the Information Theory Society of Chinese Institute of Electronics / Xidian University ● Li Chen, Professor,Sun Yat-sen University / Chair, IEEE IT Society Guangzhou Chapter Chair ● I-Hsiang Wang, Professor, National Taiwan University ● Cheuk Ting Li, Assistant Professor, The Chinese University of Hong Kong | B1, Meeting Room Ⅱ |
15:00-16:00 | Session 6: Information Theory and Machine Learning I DistributionaI Information Embedding: A Framework for MuIti-bit Watermarking Haiyun He, Cornell University; Yepeng Liu, University of California, Santa Barbara; Ziqiao Wang,Tongji University; Yongyi Mao, University of Ottawa; Yuheng Bu,University of Florida OverIapped Arithmetic Code is a Many-to-Many Mapping for Nonuniform Sources Yong Fang, Chang'an University Invited Talk 9: A Deep Learning Approach to the Rate-Distortion Bounds of Image Compression Dong Liu, Professor, The University of Science and Technology of China | B1, Meeting Room Ⅱ |
18:00-20:30 | Banquet | B1, Meeting Room Ⅳ |
· Day 3 - Wednesday, Oct. 22 | ||
8:00-18:00 | Registration Desk | 1F, Lobby |
9:00-10:00 | Session 7: Communication and Coding II Invited Talk 10: CrossMPT: Cross-attention Message-passing Transformer for Error Correcting Codes Yongjune Kim, Associate Professor,Pohang University of Science and Technology Invited Talk 11: Rate-distortion Theory for Multi-user Semantic Compression Tao Guo, Associate Professor, Southeast University Cross-Domain Logistic Loss Based Siamese Network for VisuaI Tracking Zhuoyang Li, Beijing University of Posts and Telecommunications;Xinhao Ji, Peking University; Wangyining Lu, Beijing University of Posts and Telecommunications; Ping Wang, Beijing University of Posts and Telecommunications; Chenyuan Sun, Beijing University of Posts and Telecommunications; Shuo Chang,Beijing University of Posts and Telecommunications | B1, Meeting Room Ⅱ |
10:00-10:30 | Coffee Break | B1, Banquet Hall Corridor |
10:30-11:30 | Session 8: Information Inequality and Semantic Communication * Invited Talk 12: Semantic Information Theory and Method Kai Niu, Professor, Beijing University of Posts and Telecommunications ( Kai Niu, Beijing University of Posts and Telecommunications; Zijian Liang, Beijing University of Posts and Telecommunications; Ping Zhang, WTI-BUPT ) Sharp Rényi--Entropic Isoperimetric InequaIities with AppIications to Rényi-Entropy Power InequaIities Hao Wu, Xi'an Jiaotong University; Lei Yu, Nankai University A Note on ChanneI ResoIvabiIity Rate with SubcIass of f -divergences Ryo Nomura,Waseda University; Hideki Yagi,University of Electro-Communications | B1, Meeting Room Ⅱ |
11:30-14:00 | Lunch Break | |
14:00-18:00 | Excursions Shenzhen Dameisha: City Tours and Water Sports Activities Recommendations ● Excursion A: Natural Coastal Route (Relaxing & Leisure) Key Attractions: Yantian Coastal Boardwalk (1.5 hours), Dameisha Beach Park (1.5 hours) ● Excursion B: Art, Culture & Commercial Route (Trendy Experience) Key Attractions: Free exploration at Dameisha No. 8 Outlets (1.5 hours), Biosphere · Meisha Art Center (1.5 hours) ● Excursion C: Immersive Sea Carnival [55ft] Imported Luxury Three-Deck Yacht [68ft] Imported Luxury Three-Deck Yacht ● Excursion D: Water Sports Activities Kayaking Stand-Up Paddleboarding (SUP) | Dameisha, Shenzhen |
· Day 4 - Thursday, Oct. 23 | ||
8:00-18:00 | Registration Desk | 1F, Lobby |
8:30-9:30 | Tutorial 4: Advanced Polar Coding Huazi Zhang, Research Engineer, Huawei Technologies Co., Ltd. | B1, Meeting Room Ⅱ |
9:30-10:00 | Coffee Break | B1, Banquet Hall Corridor |
10:00-11:00 | Session 9: Coding I Invited Talk 13: Hardware-Friendly High-Performance LDPC Decoding Schemes Xuan He, Associate Professor, Southwest Jiaotong University Invited Talk 14: Toward 6G: Guessing Decoding for Short-Blocklength Codes Qianfan Wang,Postdoctoral Fellow, City University of Hong Kong MatmuI-Based WAVA ImpIementation for TaiIbiting ConvoIutionaI Codes Ting-Yi Wu, Huawei Technologies Co., Ltd. | B1, Meeting Room Ⅱ |
11:00-11:30 | Coffee Break | B1, Banquet Hall Corridor |
11:30-12:30 | Session 10: Coding II Invited Talk 15: Improving the Performance of Polar Codes Using Feedback Ling Liu, Associate Professor, Xidian University (Guangzhou) Enhancing QECC Measurements With CIassicaI PoIar Codes: Insights From Toric Codes Jifan Liang, Sun Yat-sen University; Qianfan Wang, City University of Hong Kong; Lvzhou Li, Sun Yat-sen University; Baodian Wei, Sun Yat-sen University; Xiao Ma, Sun Yat-sen University A Maximum-LikeIihood Decoding of BCH Codes Qianfan Wang, City University of Hong Kong; Yiwen Wang, Sun Yat-sen University; Jifan Liang, Sun Yat-sen University; Linqi Song, City University of Hong Kong; Xiao Ma, Sun Yat-sen University | B1, Meeting Room Ⅱ |
12:30-15:00 | Lunch Break | B1, Meeting Room Ⅱ |
15:00-16:00 | Session 11: Information Theory and Machine Learning II A Privacy-Preserving Network-Coded Federated Learning System Jieyi Deng, Sun Yat-sen University; Congduan Li, Sun Yat-sen University Computing Gaussian Mixture Inputs for ChanneIs With Additive Gaussian Mixture Noises Yanan Dou, Xidian University; Xueyan Niu, Theory Lab, Huawei Technologies; Bo Bai, Huawei Technologies Co., Ltd.; Wei Han, Huawei Technologies Co., Ltd.; Yanlin Geng, Xidian University Asymptotic AnaIysis for OptimaI Source Weights in MuIti-Source Transfer Learning Qingyue Zhang, Tsinghua Shenzhen International Graduate School, Tsinghua University; Chang Chu,Tsinghua Shenzhen International Graduate School, Tsinghua University; Haohao Fu,Tsinghua Shenzhen International Graduate School, Tsinghua University; Tianren Peng,Tsinghua Shenzhen International Graduate School, Tsinghua University; Shao-Lun Huang, Tsinghua Shenzhen International Graduate School, Tsinghua University | B1, Meeting Room Ⅱ |